Securing Your Crypto Assets: Best Practices for Protecting Your Portfolio
Over half a year in 2025, the cryptocurrency ecosystem has already suffered losses totaling more than 2.17 billion dollars in hacks, exploits, and thefts, and already exceeding numerous previous annual amounts. The most notable of them was the Bybit hack in February, which involved a cold wallet attack that emptied out 1.5 billion dollars of assets. These shocking statistics provide a vivid realization: security is no longer a choice- it is survival.
It is on this background that your crypto portfolio needs protection, and this is not a mere practice, but a must! It doesn’t matter whether you are a Bitcoin or Ethereum, or dozens of altcoins: your digital assets require strict security in all wallets, as well as exchanges, and in daily use.
This guide will cover the best practices of securing your crypto assets regardless of hardware, software, behavioral, and institutional. We will tap into on-chain data, industry reports, and experience to assist you more effectively in protecting your holdings on a crypto exchange similar to XBO.com.
Why Crypto Security Demands Your Full Attention
1. The Scale of Threats in 2025
- According to Hacken, losses in Q1–Q2 2025 exceeded $3.1 billion, driven by access-control flaws, smart contract bugs, and scams.
- CertiK found that in H1 2025, there were 344 security incidents resulting in average losses of $7.18 million per incident.
- Wallet compromise was the costliest vector: $1.7 billion stolen across just 34 incidents.
- Meanwhile, the Bybit hack remains one of the largest in history, putting exchanges in the crosshairs.
These numbers show that no part of the stack is safe by default—users, wallets, protocols, and exchanges alike face relentless pressure.
2. On-Chain Clues of Risk & Inactivity
One key on-chain signal to watch: dormant coins. More than 45% of all Bitcoin hasn’t moved in over 6 months, suggesting long-term holding or abandonment. Meanwhile, analyses estimate that 2.3 to 3.7 million BTC are permanently lost—equating to 11–18% of total supply. These missing coins reduce usable supply and make security even more precious.
Glassnode also tracks “hodled or lost” coins, estimating that ~7.7 million BTC fall into that category. All these points point to a landscape where assets must be vigilantly guarded—lost or stolen coins rarely ever return.
Securing Crypto Asset Best Practices
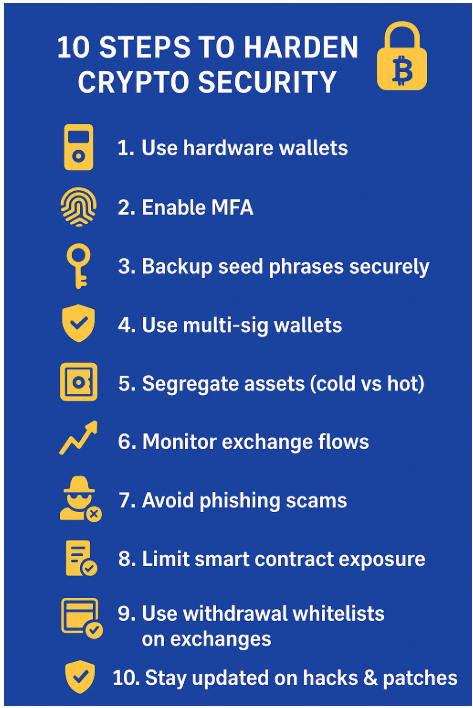
Source ChatGPT
In order to create a bulletproof defense, one can think in layers- cold storage, daily routine. These are the time-tested strategies:
1. Use Hardware Wallets (Cold Storage).
- Never leave the major part of the assets online. A hardware wallet (Ledger, Trezor, etc.) is a storage device to hold the keys, not connected to the internet.
- Select passphrase options (where available) to ensure your keys are not an unsecured seed phrase, but one secured by a second level.
- Never share your seed phrase or write it down digitally. If your seed escapes, your wallet can be emptied instantly.
2. Segregate Assets by Risk
Divide your holdings into tiers:
- Cold storage / long-term holdings
- Hot wallets for trading / everyday use (minimal amounts)
- Smart contract exposure — Only lock amounts you can afford to lose
This way, a breach of your hot wallet doesn’t drain your entire portfolio.
3. Apply Multi-Signature & Smart Controls.
- Multi-signature can be implemented on some wallets (e.g., Gnosis Safe), which means that many keys are required to approve transactions.
- For self-custody DeFi strategies, use timelocks or safe modules to limit contract interactions.
- Many institutions use threshold signature schemes to split trust among multiple parties.
4. Third-Party Contracts Audit and Review.
- Prior to dealing with new protocols, verify independent security audits.
- Check the code and legitimacy of the contract with the help of such tools as Etherscan.
- Watch out for copycat/phishing imitators – always check the domain and source code.
5. Implement Hard Authentication and Access Control.
- Use multi-factor authentication.
- Be aware of any type of phishing sites.
- Activate the use of passwords to create strong passwords, which are unique to each service.
- Make it possible to withdraw whitelist only (send to known addresses).
6. Monitor Exchange Flows and On-Chain Alerts
- Use analytics to spot large exchange inflows/outflows, which often presage price or security events.
- Install address monitoring alerts (through block explorers or wallet-providers) to get an alert should there be any unintended transfers.
7. Maintain Backups
- Think of the backup separation (Shamir in Secret Sharing).
- Store backups in safe sites.
8. Be Alert to Social Engineering & Phishing Attacks
- Always verify URLs and sender addresses before entering credentials.
- Do not approve transactions blindly—review amounts and contract code before signing.
- Be cautious of unsolicited messages, “airdrop” offers, or impersonation scams.
9. Limit Smart Contract Exposure
- If you stake or lend via DeFi, only commit funds you can afford to lose.
- Use protocols with transparent audits and insurance funds.
- Avoid interacting with unverified or anonymous contracts unless thoroughly vetted.
10. Insurance & Risk Mitigation
- Some custodial services or protocols offer insurance against hacks—consider using them for part of your exposure.
- Spread into several wallets/services- do not put all eggs in the same basket.
- Keep up to date: update your devices and firmware to keep out of exploits.
Case Study: Lessons from the Bybit Hack & Others
The February 2025 Bybit cold wallet exploit remains one of the most alarming breaches in crypto history, with $1.5 billion in theft. This exploit exploited access to the offline wallet—underscoring that “cold” does not always mean immune.
Other notable incidents in 2025 include:
- Cetus Protocol hack: $225 million stolen via smart contract vulnerability
- Over 344 security incidents in H1 alone across wallets, phishing, and protocol exploits
- Over 2.47 billion total stolen in H1 2025.
These incidents emphasize the fact that even such big and famous platforms may fall down, that is why the issue of self-protection should not be negotiable.
Integrating Security with Accessibility: Using Platforms Safely
Even as you build fortress-level defenses, many users still rely on centralized interfaces or bridging platforms, whether for trading, staking, or yield. If you use a Crypto Exchange Platform, follow these additional safety measures:
- Use withdrawal whitelisting so that funds can only flow to your known cold addresses.
- Allow multi-factor withdrawals or multi-sign withdrawals where possible.
- The platform should have proof-of-reserves statements or audit statements, which must be verified.
- Let the cold wallets or sub-accounts be used in transferring the large sums in or out.
- Limit session times and logout automatically when idle.
Data-Driven Insights You Should Monitor
- Dormant supply metrics: Watch the share of coins that haven’t moved in >1 year (Glassnode’s “Supply Active More 1Y”). Sudden shifts may signal accumulation or whale movements.
- Exchange net inflows/outflows: When a sell pressure usually does come before a large inflows; when a confidence can be a clue of some large outflows. Tracking Track real-time using analytics dashboards.
- Access-control incident statistics: Keep up with reports from CertiK, Hacken, Chainalysis, etc., to understand emerging threat patterns.
These metrics give you early warnings—not guarantees—but help you stay ahead.
Conclusion: Defense Is the Best Offense
Crypto security is not a one-time setup—it’s a mindset, a routine, and a multi-layered system. Complacency is more costly, with billions already lost by 2025.
Through the integration of hardware defenses, alerting behavior, auditing of the contract, analytics monitoring, and platform-specific safeguards, you can greatly mitigate your risk. Smartly use your Crypto Exchange Platform: keep exposure to a minimum, use advanced security services, and send big balances to self-custody infrastructure. Always keep in mind that the protocols and platforms will never remain the same, though the best way to defend is to have control over the keys and control your habits.
In the world of digital assets, your keys are your destiny. Be secure. Be vigilant. And let your portfolio survive when storms come.
0 Comments
Leave a comment